The potential risks associated with oversharing in Microsoft 365 can jeopardize the security of sensitive information. It is essential to recognize and mitigate the contributing factors order to protect data and prevent breaches, particularly when utilizing AI tools like Copilot.
In this article, we will delve into the concept of "oversharing" in Microsoft 365, examining the associated risks and providing guidance on how to identify and address it.
What is Oversharing in Microsoft 365?
Let's start with a simple definition:
Oversharing: the act of sharing access to content and information, beyond the needs of the recipient.
For example, one time many years ago, I was accidently given access to a document library that had a ton of confidential staff information.
I only needed access to one specific spreadsheet that was already openly shared with staff. However, my colleague had sent me a link to the folder containing the spreadsheet, instead of the file.
That folder contained sensitive staff information that I knew I was not permitted to see. That is oversharing.
Imagine coming to work one morning to find out that your company had a major data breach. Imagine finding out that you or someone you work closely with was involved in the events that led up to that breach.
Fast forward five years and imagine what would happen if employees discovered they could access confidential information from a simple AI prompt with Microsoft's Copilot? Not because they had malicious intent, but because that employee simply had access to data that they shouldn't have.
The ability to overshare company data introduces risks to the organization. AI tools like Copilot can increase that risk by making it easier for the average person to discover sensitive information that they might not have known they had access to.
I'll cover the risks in more detail later in this article, but first, let's look at the factors that can lead to oversharing.
How Can Content be Overshared?
So what went wrong in that little story above? How did that person end up oversharing confidential information with me?
Was it a training issue? Was it because the department had stored that shared spreadsheet alongside confidential documents? Was it because they didn't have sensitivity labels in place?
If your answer was "All of the above", you're on the right track. Here are some examples of how oversharing can occur:
Creating New Links Every Time Something is Shared
Share links provide a fast and relatively simple way to share and collaborate on files across our organization and externally. However, do you staff know how to re-use existing links or do they create a NEW one every time?
How does this contribute to oversharing? The more share links created, the more paths people have to your sensitive content.
For example, an HR department may store all of their resumes, cover letters, job descriptions, contracts, and other sensitive files on their private SharePoint site. To collaborate with people across the organization and externally, they will depend on share links.
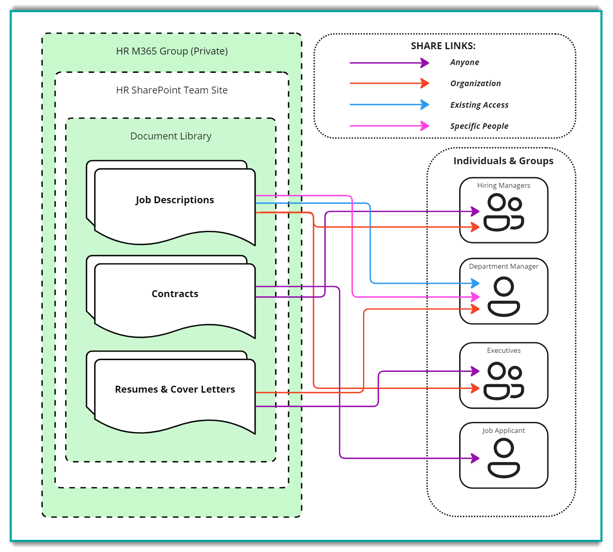 Files and folders can have several share links created for different individuals and groups
Files and folders can have several share links created for different individuals and groups
While convenient, share links can override container-level permissions, such as M365 Groups, SharePoint sites, and document libraries.
Imagine investing a bunch of money into securing your home with new doors, locks and alarm system. How secure would that house really be if you and your family hand-out copies of your key and security code every day?
.png?width=603&height=727&name=blog-feb13-6-min%20(1).png) How many people and groups are your files shared with?
How many people and groups are your files shared with?
The average M365 user will use the default share option when sending a file to a colleague. Next, let's look into how that can also contribute to oversharing.
The Default Share Link Type
What is the default share link for your organization?
TIP: If your default is "Anyone with a Link", you should to talk to your IT admin today.
Most of the customers we work with typically use the "People in your Organization" link that includes EDIT access. While being an internal-only link makes it reasonably safe, is it the BEST option for you?
How does this contribute to oversharing? Every time someone uses "People in your Organization", "Anyone with the link", or "People you choose" - they're creating a NEW share link. Even if the people they're sharing with already have access.
Using my example from earlier, that's like giving a family member a new copy of the house key every time they need to get inside. While it works in the short term, you may be slowly weakening the security of your home.
The only share link that respects existing permissions is called "People with Existing Access". This one doesn't override existing permissions and, in my own opinion, makes for a great default share link type for most use cases.
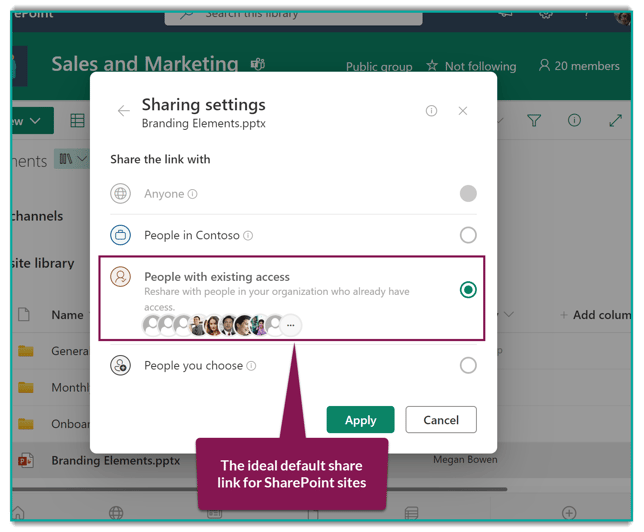
By using "People with existing access" as the organization default, you can help reduce the number of NEW share links being created. Users will need to make an active choice to change it to something else.
Creating the wrong share link can expose sensitive and confidential files to the wrong people over time. Copilot is expected to expose just how widely shared our sensitive communication and files really are.
Next, let's look at how share links can be secured with sensitivity labels.
Sensitivity Labels Are Not Configured
Sensitivity labels add extra layers of protection on confidential files and messages. For example, you can create a label that (1) adds a custom watermark to documents and emails, (2) encrypts the content, and (3) prevents unauthorized access to sensitive access - even with share links.
How does not having Sensitivity Labels contribute to oversharing? Without sensitivity labels, you are missing an important layer of protection for your confidential content.
For example, let's say the HR manager has prepared a spreadsheet for upper management that outlines staff salaries, but they accidentally emailed the entire organization.
- WITHOUT sensitivity labels, there would be little to stop staff from opening that document and seeing everyone's salaries.
- WITH sensitivity labels, they can be blocked from opening the document. Even if it was shared using the "People in the Organization" share link.
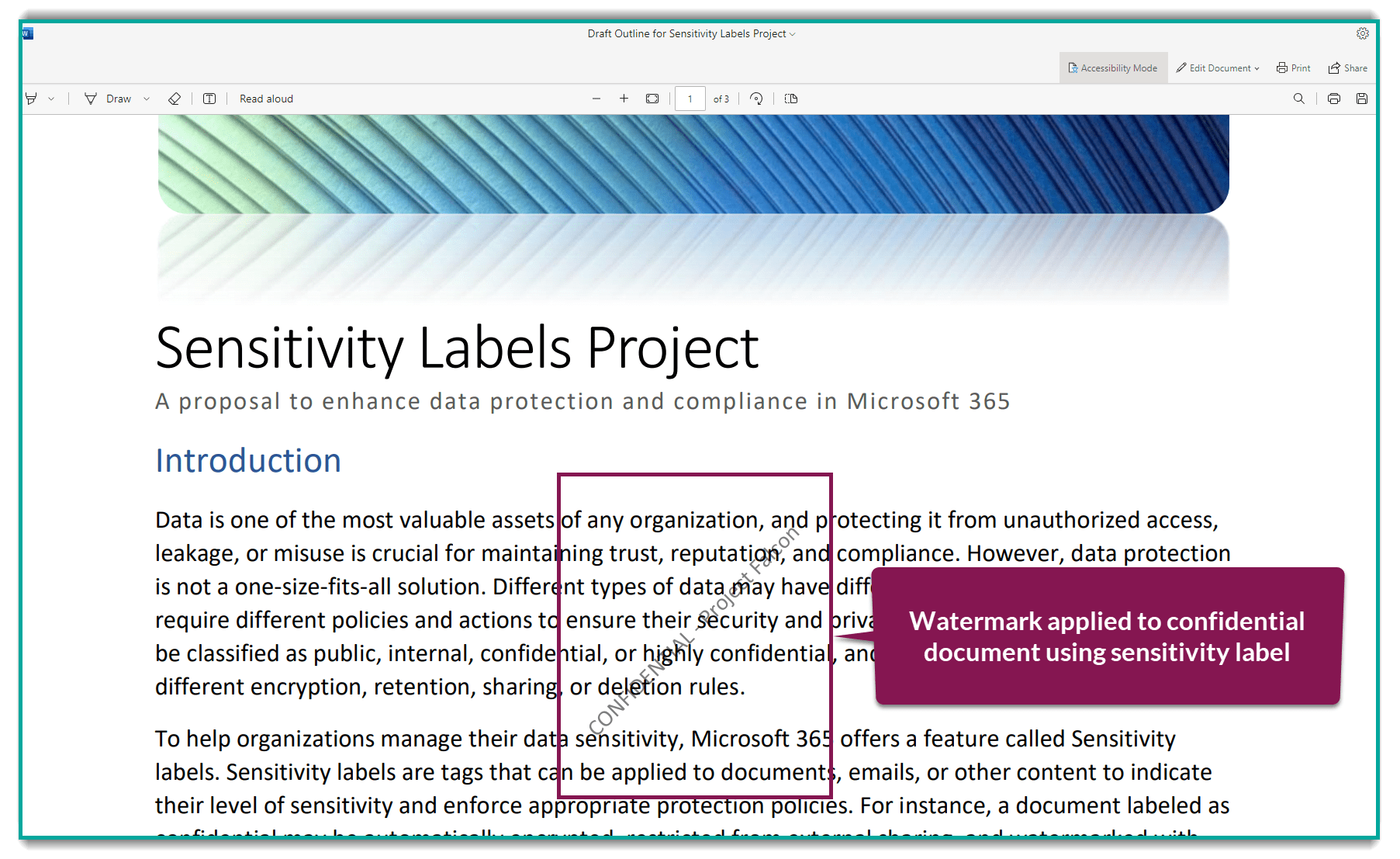
Copilot factors sensitivity labels in its responses too.
Sensitivity labels are not configured out-of-the-box in M365. If staff at your organization handle a lot of confidential information, you will want to start planning what kind of protection your content needs before creating your first label.
Now let's look at a few ways you can identify oversharing in M365.
How to Identify Overshared Content in Microsoft 365
Uncovering and addressing oversharing in M365 has never been an easy task. Global admins do get a few tools that can help.
The Data Access Governance reports in the SharePoint Admin center include "Sharing links" reports that can help identify where oversharing is occurring for up to 10,000 sites. However, you will need to run a separate report for each share link type, and they can only be run once every 24 hours.
Additionally, these reports do NOT include OneDrive data.
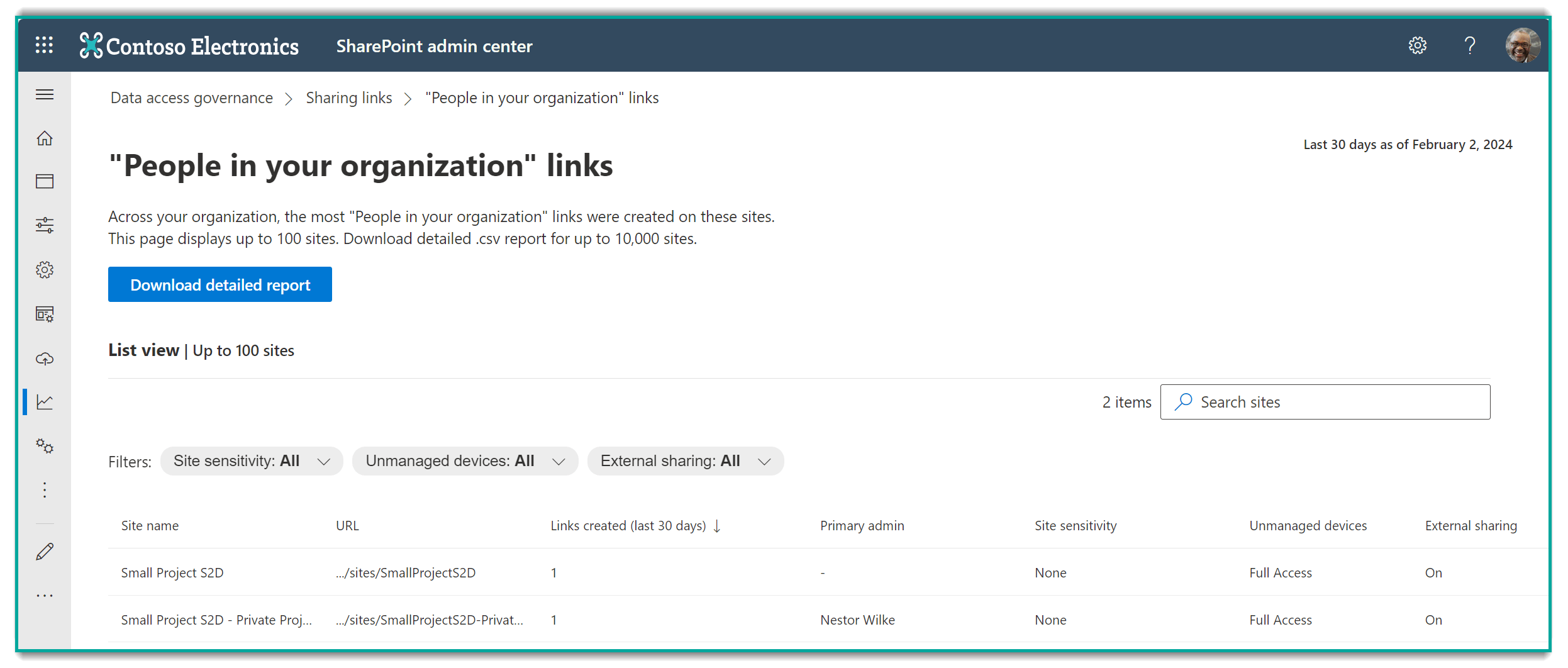
The Microsoft 365 Usage Reports can provide a quick tally of the number of files users have shared internally and externally. It doesn't provide specifics, but you can use these reports to see who the heavy-sharers are across your org.
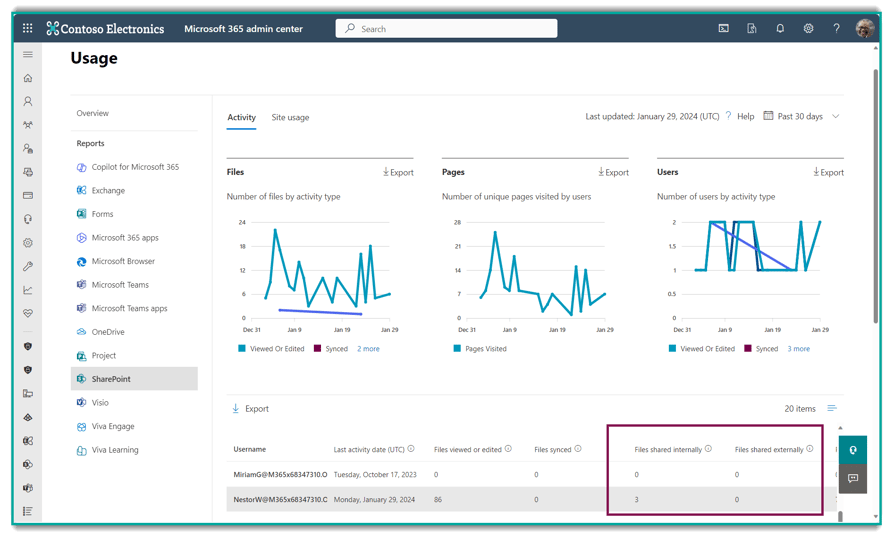
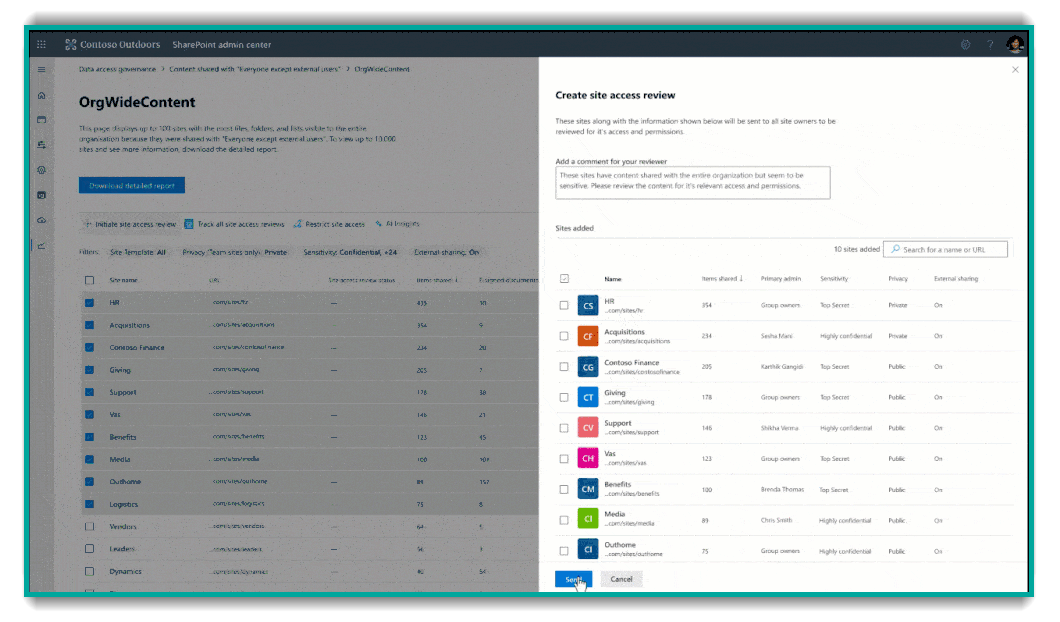
If your org is a SharePoint Premium subscriber (AKA "SharePoint Syntex"), you can run "Site Access Reviews" which is a process that triggers site owners to review and update access to files on their sites.
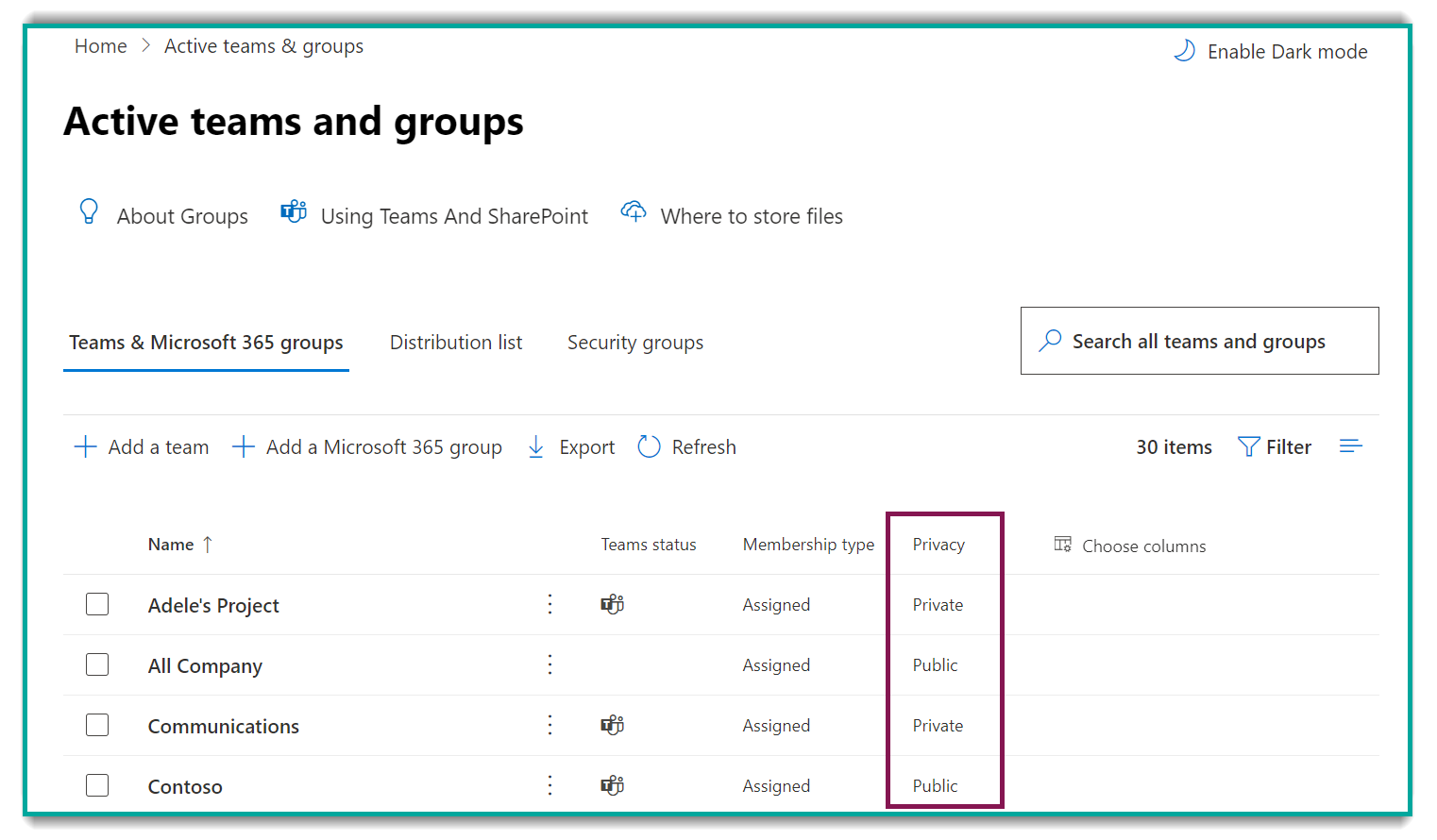
Another method you can use to check for oversharing is to audit M365 Group public/private settings from the 'Active Teams and Groups' page in the M365 Admin Center.
As mentioned earlier, oversharing can occur simply by making the wrong sites 'Public', as this can allow members to EDIT content that they shouldn't have access to.
Lastly, E5 tenants should be taking advantage of Sensitive Information Types in Microsoft Purview, which can be configured to help identify potentially sensitive info in documents, such as credit cards, personally identifiable information, and more.
Why is Oversharing a Problem for your Copilot Implementation and Other AI?
Oversharing of files and information across our organization is not a new problem. We've all been exposed to old SharePoint sites and network drives with confidential information at some point in time.
Copilot (among other AI tools) is simply bringing the issue of oversharing to the surface. Here are some of the impacts your organization may experience if Copilot is rolled out prematurely.
Does Copilot Impact Privacy and Security
To be clear, Copilot will not make your confidential data insecure. It will expose the information that is already insecure.
For example, have you ever wondered what your CEO's salary is? If that data, or the location of that data has been shared - Copilot can use it.
Your Copilot rollout could be a single prompt away from being cancelled by upper management if oversharing is not under control.
More Noise and Less Relevancy
Responses from Copilot may be full of irrelevant information simply because you have access to a lot of irrelevant content.
For example, asking Copilot to summarize your weekly sprint meetings may be polluted with information from other sprint meetings that share a similar name and/or location.
 Even AI can struggle to make heads or tails of an overabundance of conflicting information
Even AI can struggle to make heads or tails of an overabundance of conflicting information
The less information Copilot needs to sort through, the faster it will provide you with clean and accurate responses.
Copilot won't intuitively know the difference between the "Sales forecast" Excel spreadsheet you made yesterday, against the one you made last month or last year.
If your OneDrive and SharePoint libraries are full of outdated and inaccurate files and drafts - Copilot may include them in its responses.
By reducing oversharing, Copilot will have an easier time getting to the source of truth in your data.
More Hallucinations
When AI presents bad data as fact, you're dealing with a hallucination. Sometimes, the only way to catch this happening is you knowing the material well enough to recognize when you've been given bad information.
A staff member may not always know when they've been presented with bad information. If they use that bad data in their own work, the problems can compound from there.
By reducing oversharing, there will be less bad information to parse through when we make a request.
Lower End-User Trust
In my opinion, this is one of the bigger risks.
User adoption of any new tool or product takes time and effort. After you've invested time and money into preparing for Copilot, getting the licenses, and training staff - you want people to immediately GET the value it brings to their work.
We're already hearing from clients and partners about how underwhelming their initial experience with Copilot has been so far. Some are now less excited about the tool because they can't get it to provide them with good information.
And these are the early-adopters and enthusiasts who live for the shiny new tech.
If your end user's first experience with Copilot leads to bad information or confusing responses - you're in for a long uphill battle to turn that first impression around. Not only by fixing the underlying issues but by simply convincing staff to give it another chance.
How Can You Fix Oversharing with Copilot Coming?
Oversharing in Microsoft 365 poses significant risks to organizations. The ease of access to confidential information through AI tools like Copilot can lead to unintended data breaches.
Factors contributing to oversharing include creating new share links every time something is shared, using default share link types that override existing permissions, and not configuring sensitivity labels.
To effectively implement a Copilot strategy and protect sensitive information, it is crucial to address oversharing within the organization. For further assistance in managing oversharing risks and optimizing your Microsoft 365 environment, it is recommended to contact Orchestry for expert guidance and support.


/HubSpot%20-%20eBook%20-%20Proof%20Card%20Mockup%20001-min.jpg?length=10&name=HubSpot%20-%20eBook%20-%20Proof%20Card%20Mockup%20001-min.jpg)


/HubSpot%20-%20Buyers%20Guide%20-%20Proof%20Card%20Mockup%20001-min.jpg?length=10&name=HubSpot%20-%20Buyers%20Guide%20-%20Proof%20Card%20Mockup%20001-min.jpg)
/HubSpot%20-%20Features%20Sheet%20-%20Proof%20Card%20Mockup%20001-min.jpg?length=10&name=HubSpot%20-%20Features%20Sheet%20-%20Proof%20Card%20Mockup%20001-min.jpg)


 Files and folders can have several share links created for different individuals and groups
Files and folders can have several share links created for different individuals and groups.png?width=603&height=727&name=blog-feb13-6-min%20(1).png) How many people and groups are your files shared with?
How many people and groups are your files shared with?





 Even AI can struggle to make heads or tails of an overabundance of conflicting information
Even AI can struggle to make heads or tails of an overabundance of conflicting information